Set Up Authentication with OpenId Connect (OIDC)
OpenID Connect (OIDC) is a modern identity protocol that Tonkean supports to securely authenticate users. Built on top of OAuth 2.0, OIDC enables Tonkean to verify the identity of users through an external identity provider like Okta, Azure AD, or Google Workspace.
Tonkean offers a provider-agnostic option for authentication using OIDC using the well-known endpoint. If you prefer to set up identity provider-specific OIDC authentication, see either Configure Okta OpenId Connect (OIDC) or Configure Ping Identity OpenId Connect (OIDC).
Configure OIDC as Preferred Authentication Method
To set up OIDC as your preferred authentication method, follow the steps below:
In Tonkean, select your profile icon in the upper right.
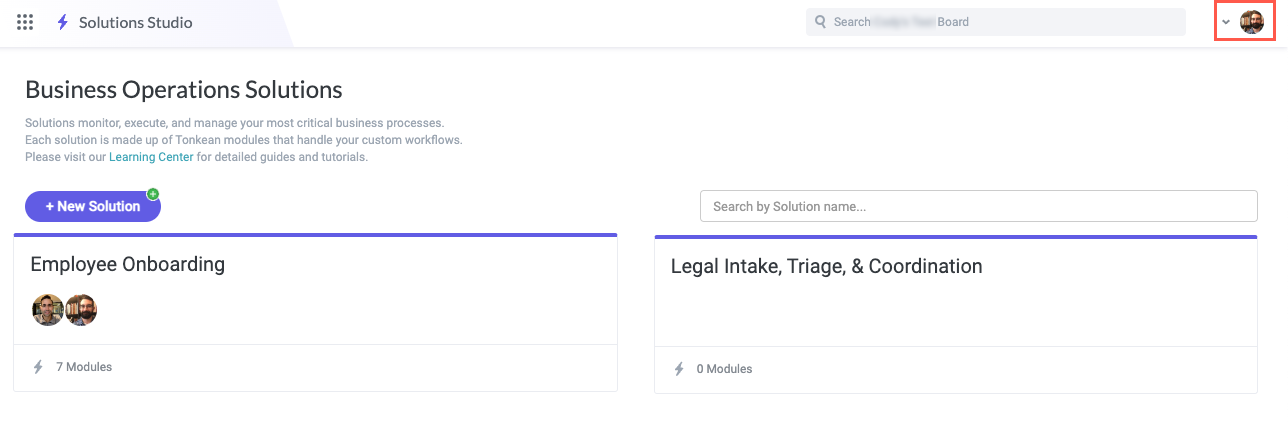
Select the <Enterprise Name> Administration in the dropdown. The Enterprise Administration screen displays.
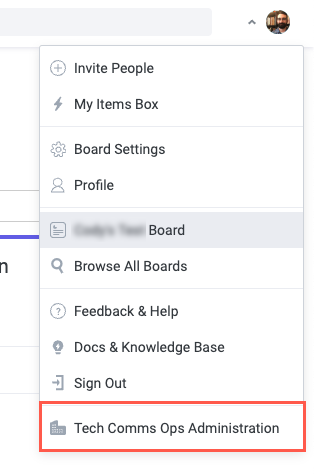
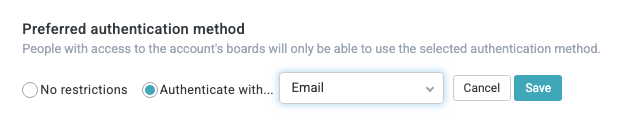
Locate the Preferred authentication method section and select No restrictions.
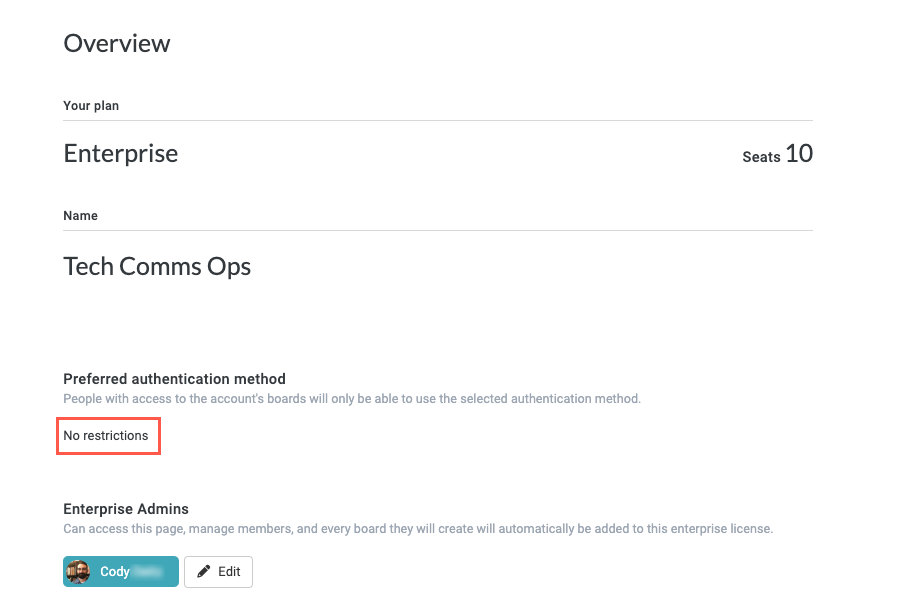
Select Authenticate with, then select OpenID Connect from the dropdown. OIDC authentication fields display.
Enter the OpenID Connect discovery Url, as well as the Client ID and Client Secret from your identity provider.
The discovery URL is also known as the well-known endpoint; it follows this pattern:
https:://{your-service-provider-root-url}/.well-known/openid-configuration.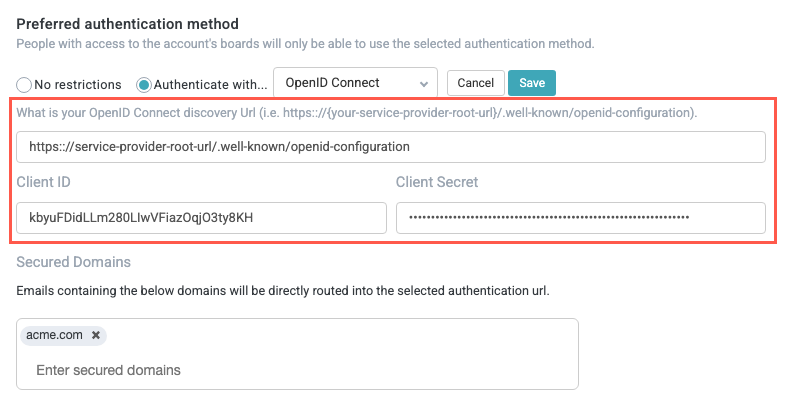
Enter the secured domains that will redirect to OIDC authentication.
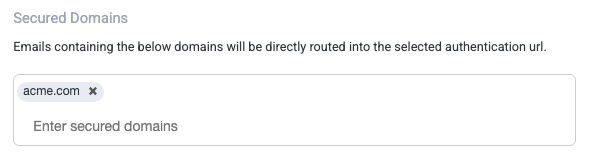
When finished, select Save. The OIDC set is complete.
When users sign in to Tonkean, they should do so with their work email and Tonkean will redirect them to the appropriate SSO login screen.
Test OIDC Authentication
Before allowing users to sign in using OIDC, we recommend testing the process:
In a different browser than the one you configured the authentication (or an incognito window), navigate to the Tonkean Sign In screen.
Enter your work email address, then select Sign In.
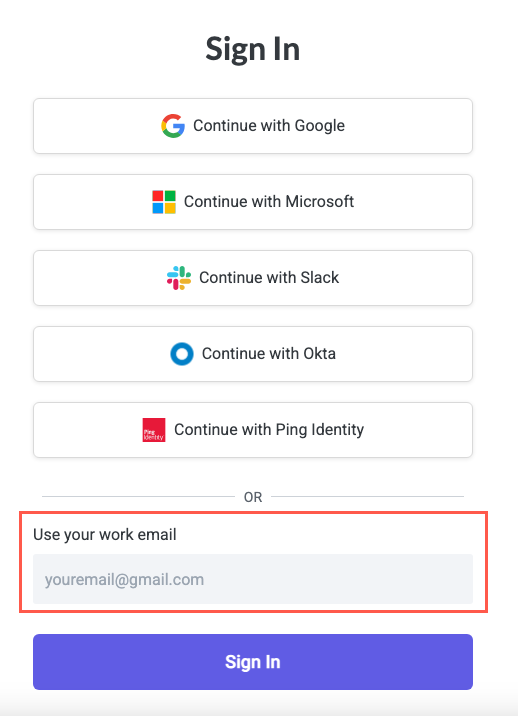
If OIDC authentication was configured correctly, you should be redirected to the relevant SSO provider to sign in. If an error occurs, you can temporarily set the authentication method to Email, which sends users a one-time token for access while you revisit the setup steps.
If you need extra help, contact Support.
Learn More
This generic OIDC configuration is recommended for most users. If you prefer to do identity provider-specific configuration (with Okta, for example), see the provider-specific topics below: